Creating an IAM Policy for Lambda Function
This section guides you through creating an IAM Policy that grants your Lambda function the necessary permissions to perform get, put, and delete operations on objects in your S3 buckets.
Configure Lambda Function Permissions
-
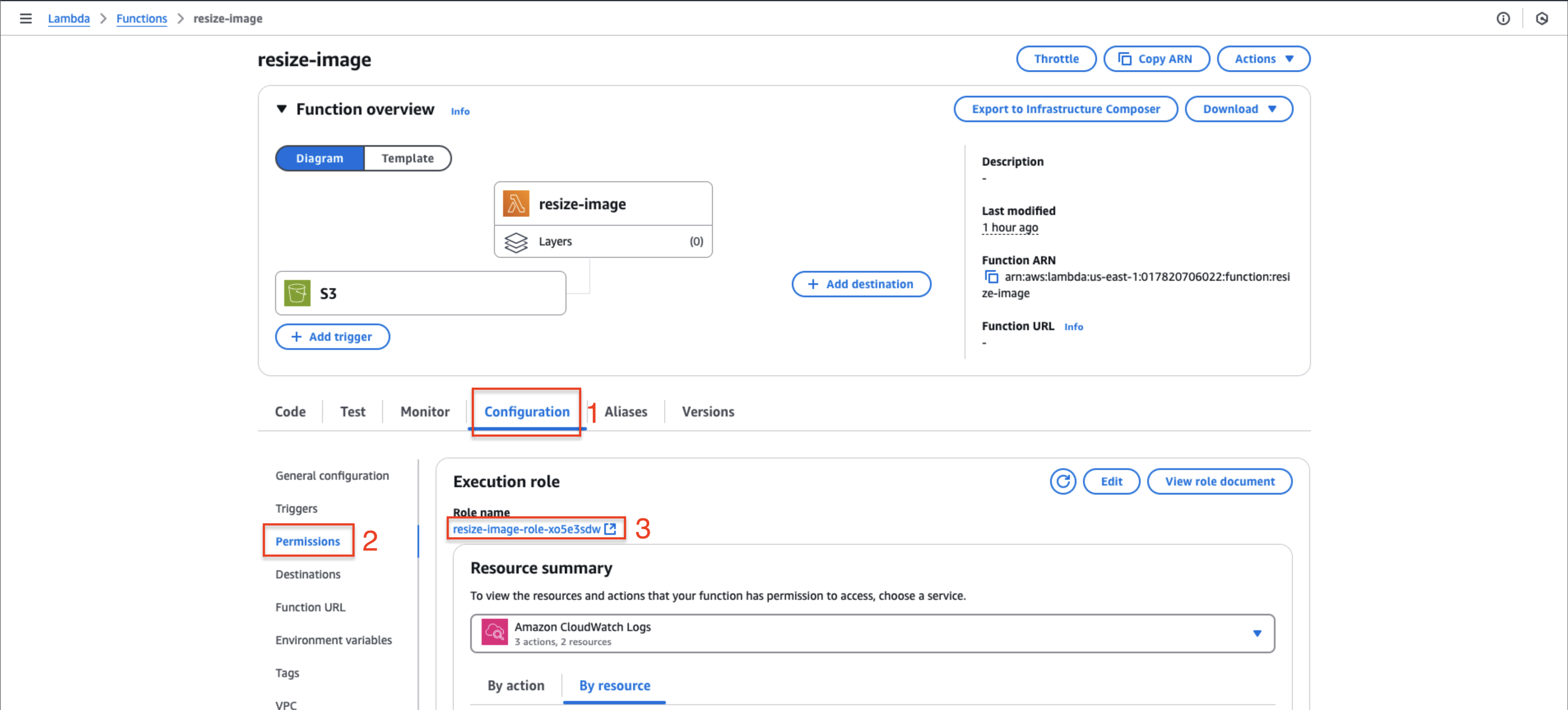
Navigate to your Lambda function configuration:
- Open the resize-image function
- Select the Configuration tab
- Click on Permissions
- Click the execution role name to access IAM
-
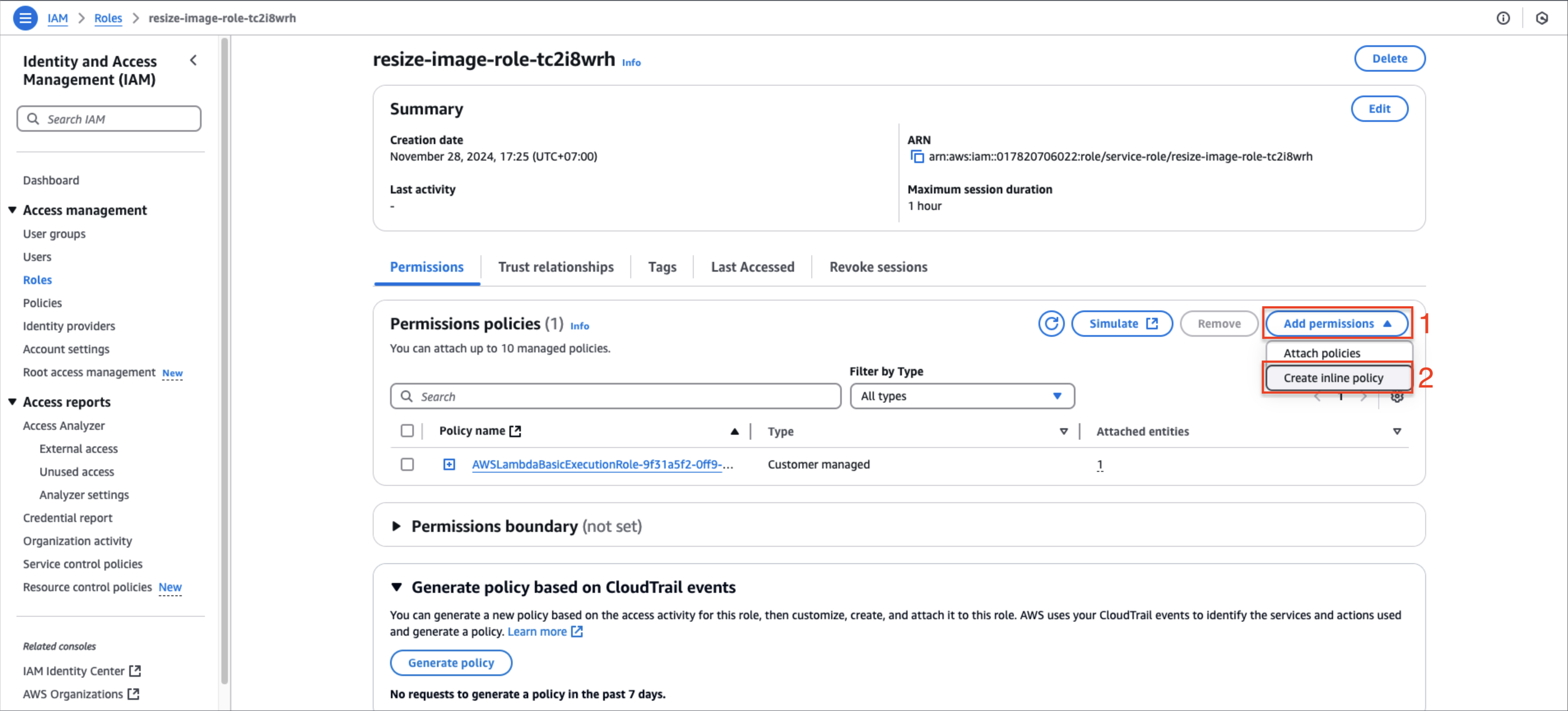
Create a new inline policy:
- In the IAM role page, select Add permissions
- Choose Create inline policy
Define S3 Permissions
-
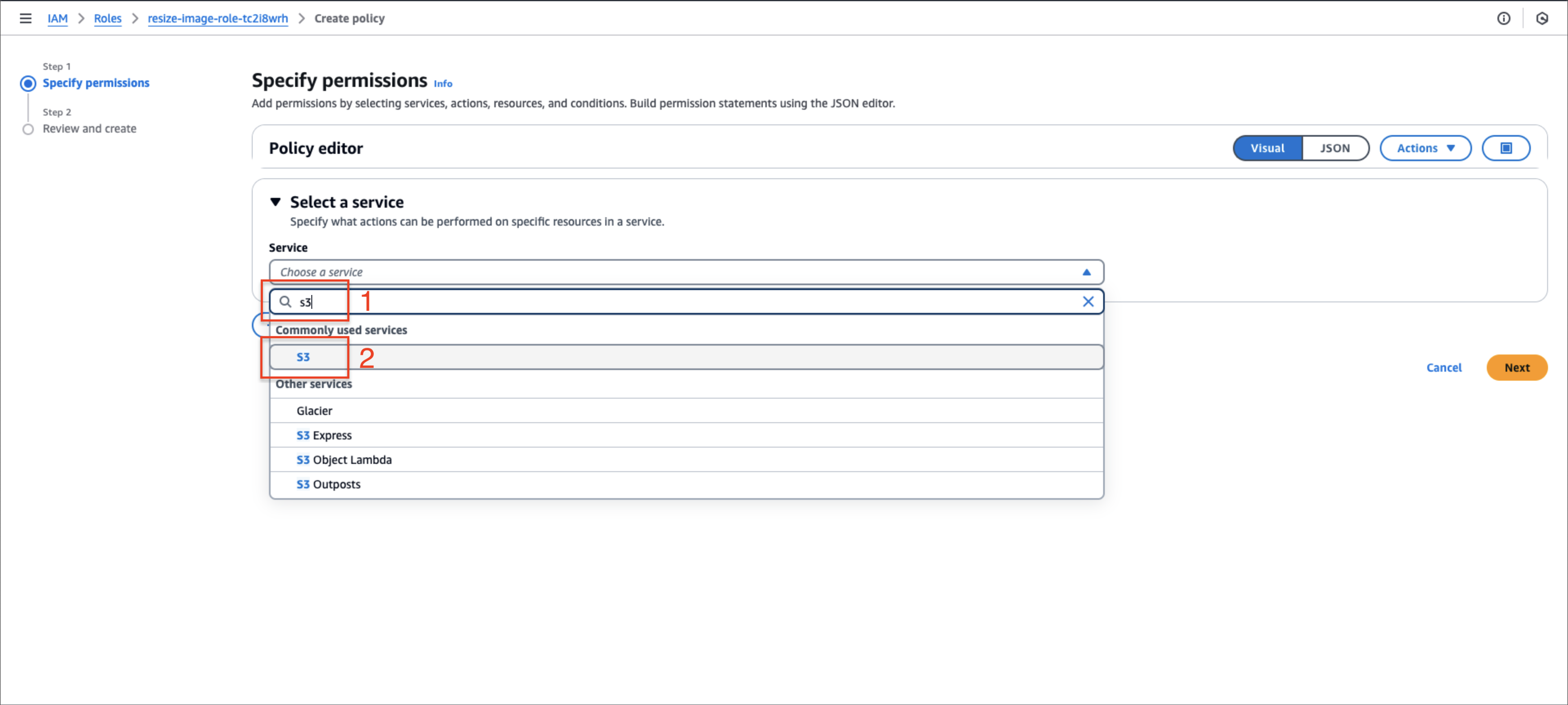
Configure source bucket permissions:
- Select Choose a service and search for S3
- Click S3 to select the service
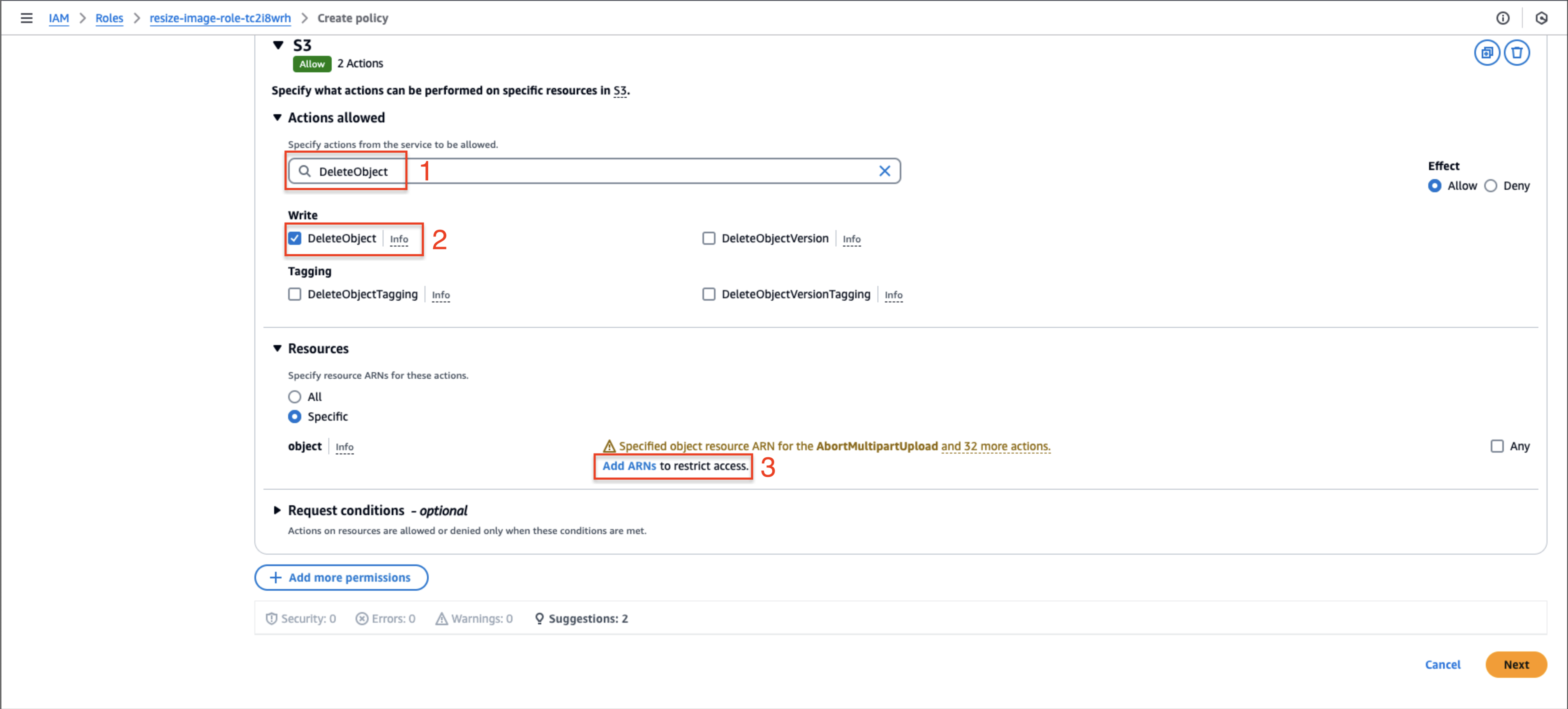
- Search for and select GetObject under Read actions
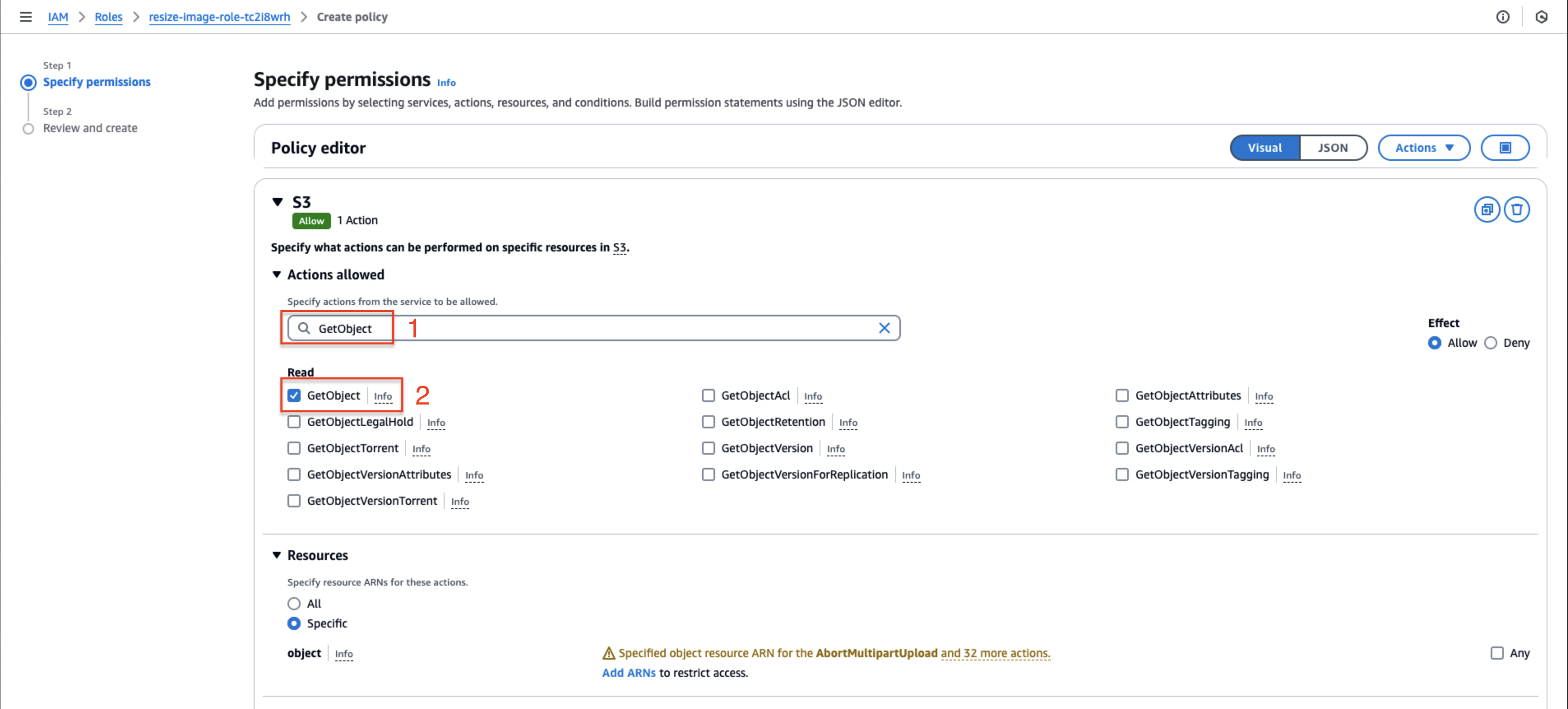
- Clear the search and add DeleteObject under Write actions
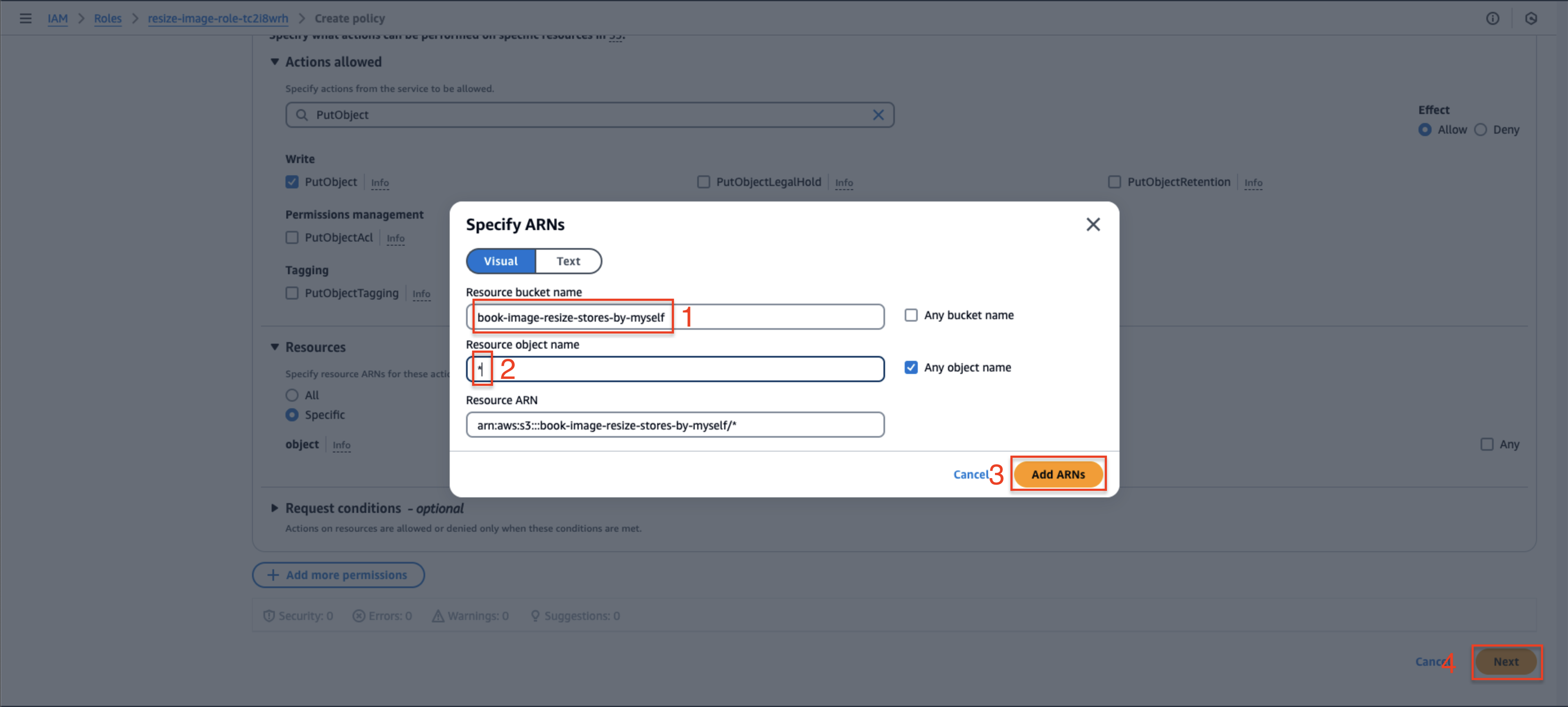
- Select Add ARNs to specify the resource
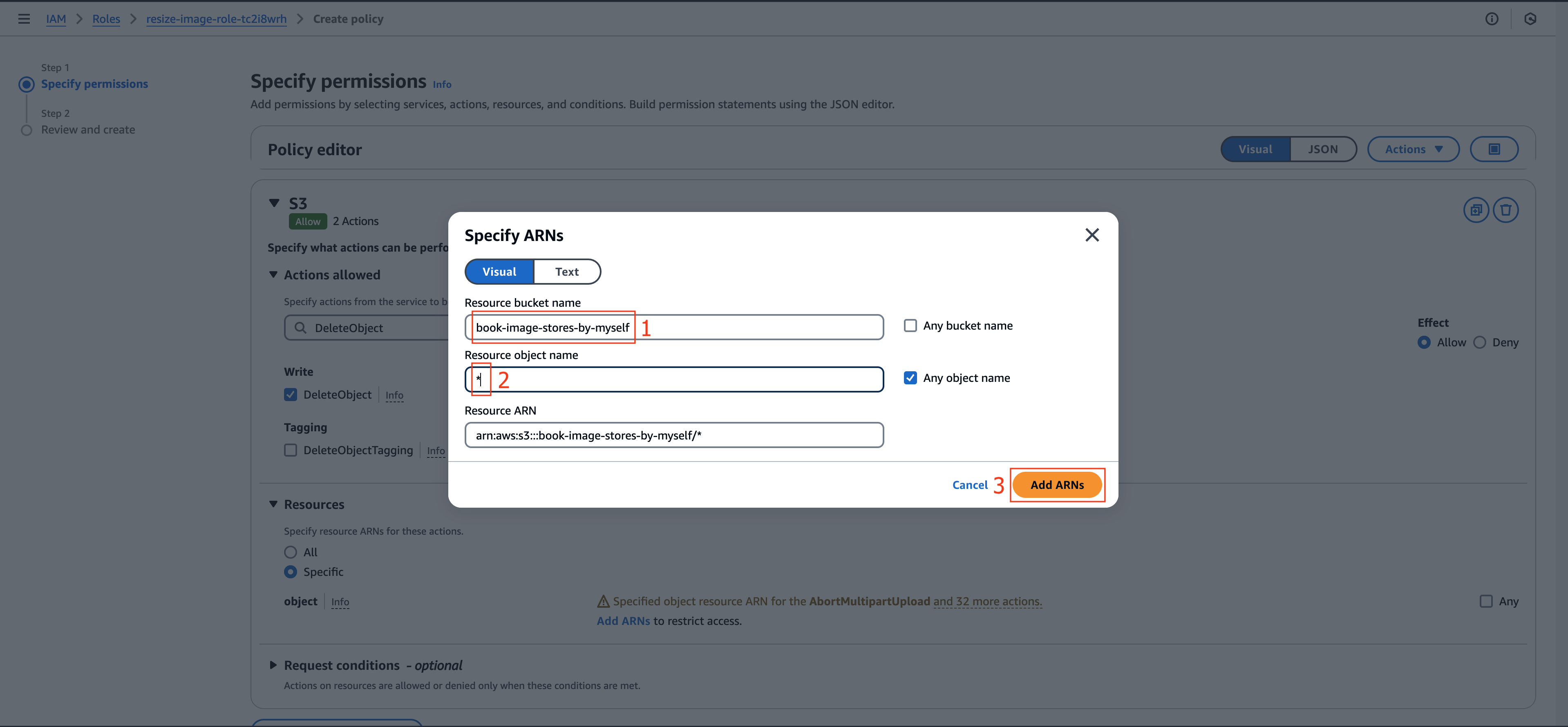
- In the Specify ARNs dialog:
- Set Resource bucket name to
book-image-stores-by-myself - Enter
*for Resource object name - Confirm with Add ARNs
- Set Resource bucket name to
-
Configure destination bucket permissions:
- Select + Add more permissions
- Choose S3 service again
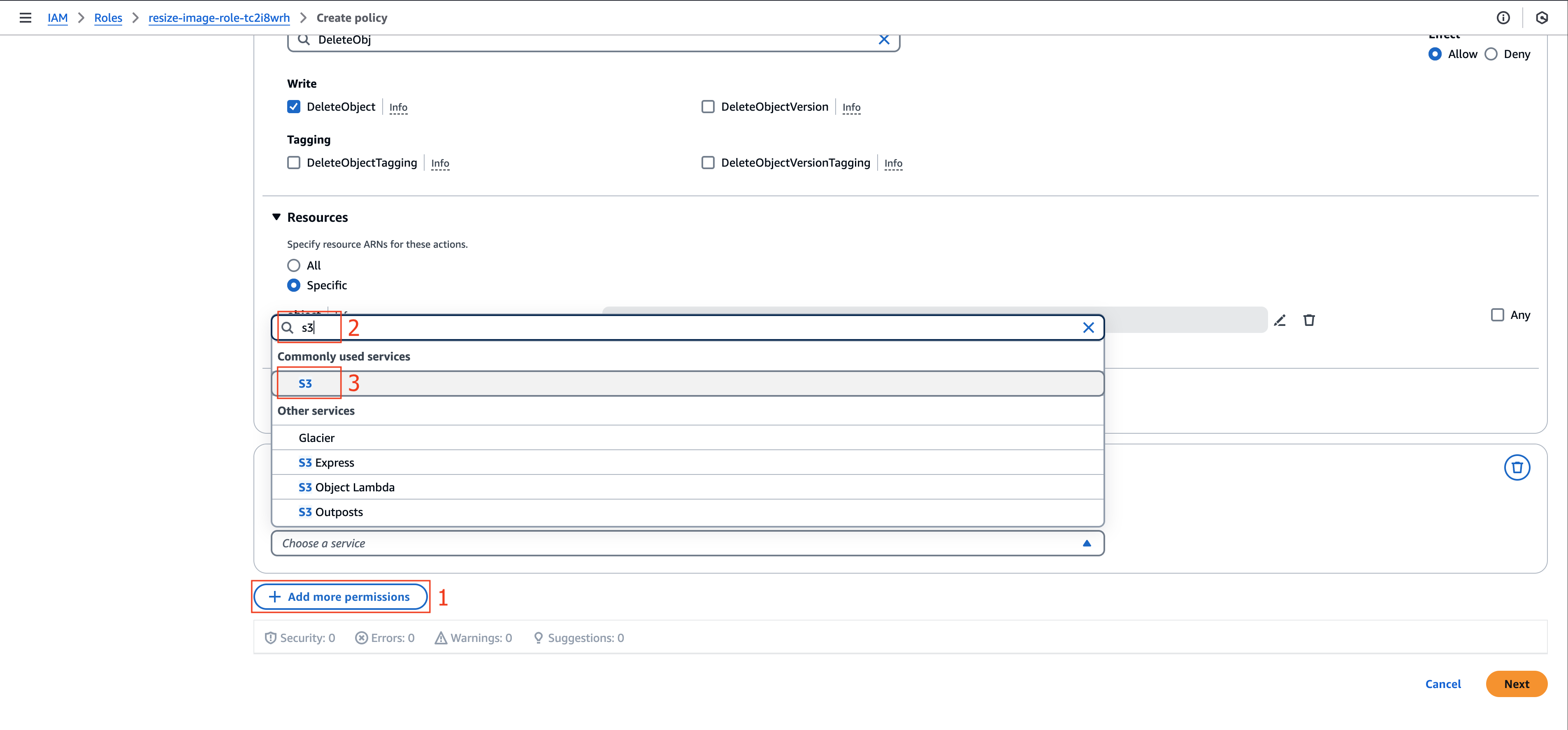
- Search for and select PutObject under Write actions
- Click Add ARNs
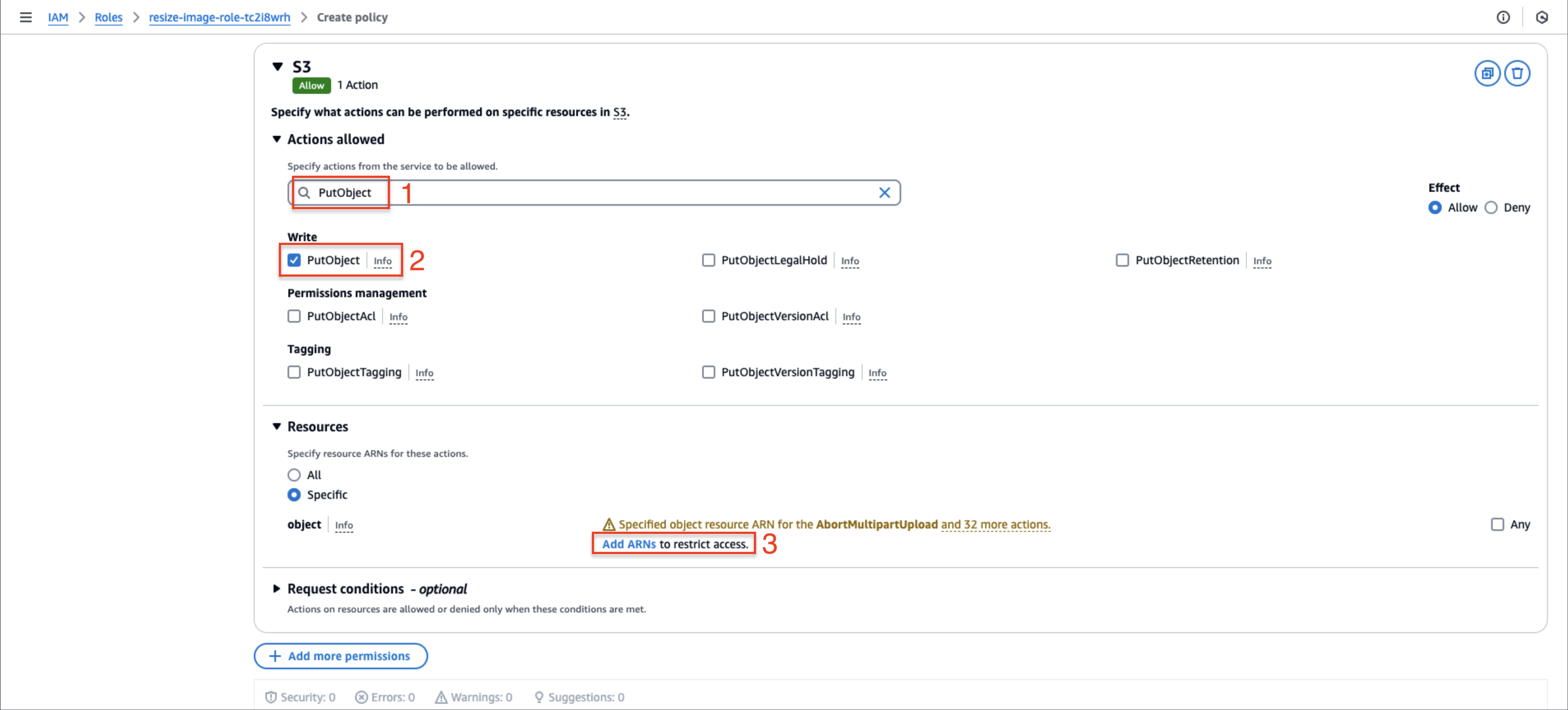
- In the Specify ARNs dialog:
- Set Resource bucket name to
book-image-resize-stores-by-myself - Enter
*for Resource object name - Click Add ARNs
- Set Resource bucket name to
- Proceed by clicking Next
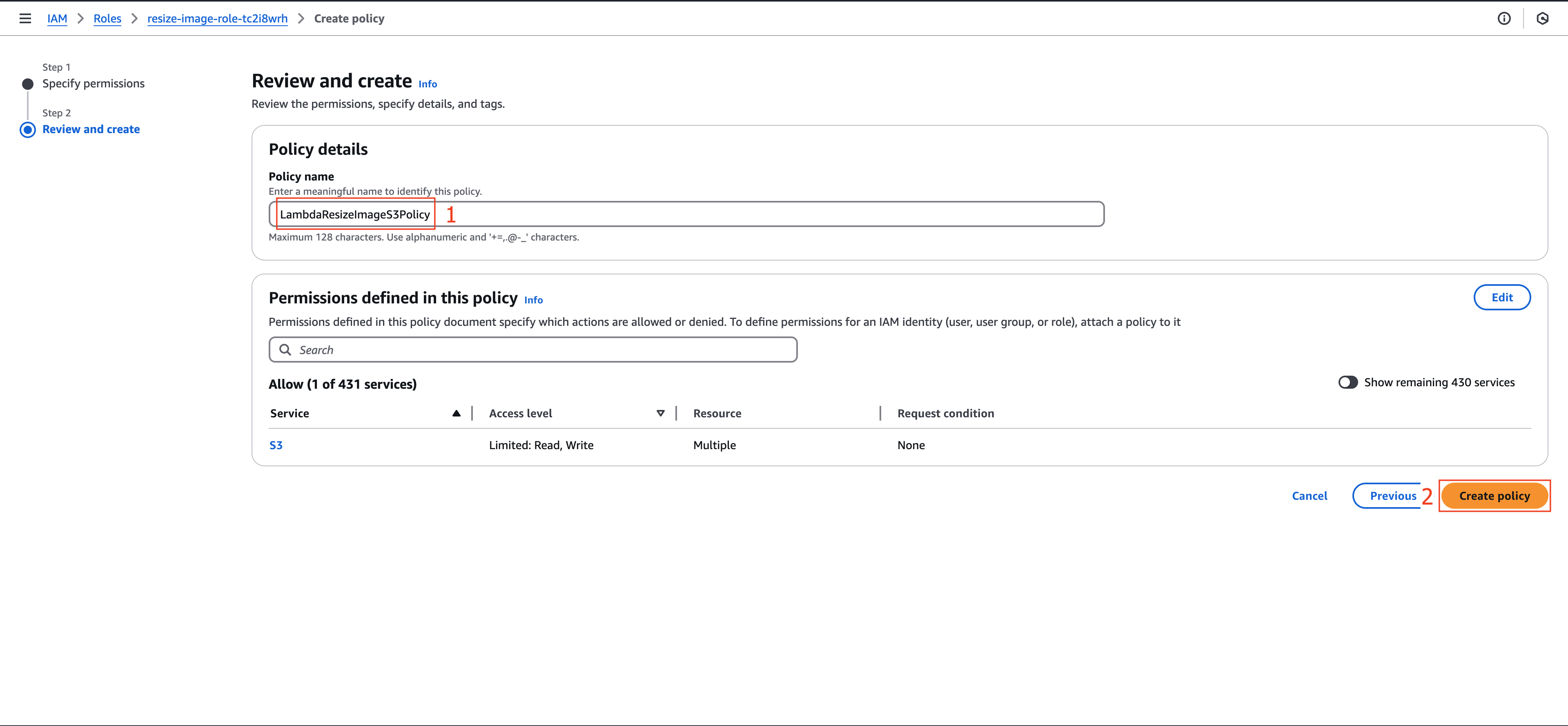
Review and Create Policy
-
Finalize the policy:
- Name your policy (e.g.,
LambdaResizeImageS3Policy) - Review the permissions configuration
- Click Create policy to finish
- Name your policy (e.g.,
-
Verify the newly created policy in the role’s permission list
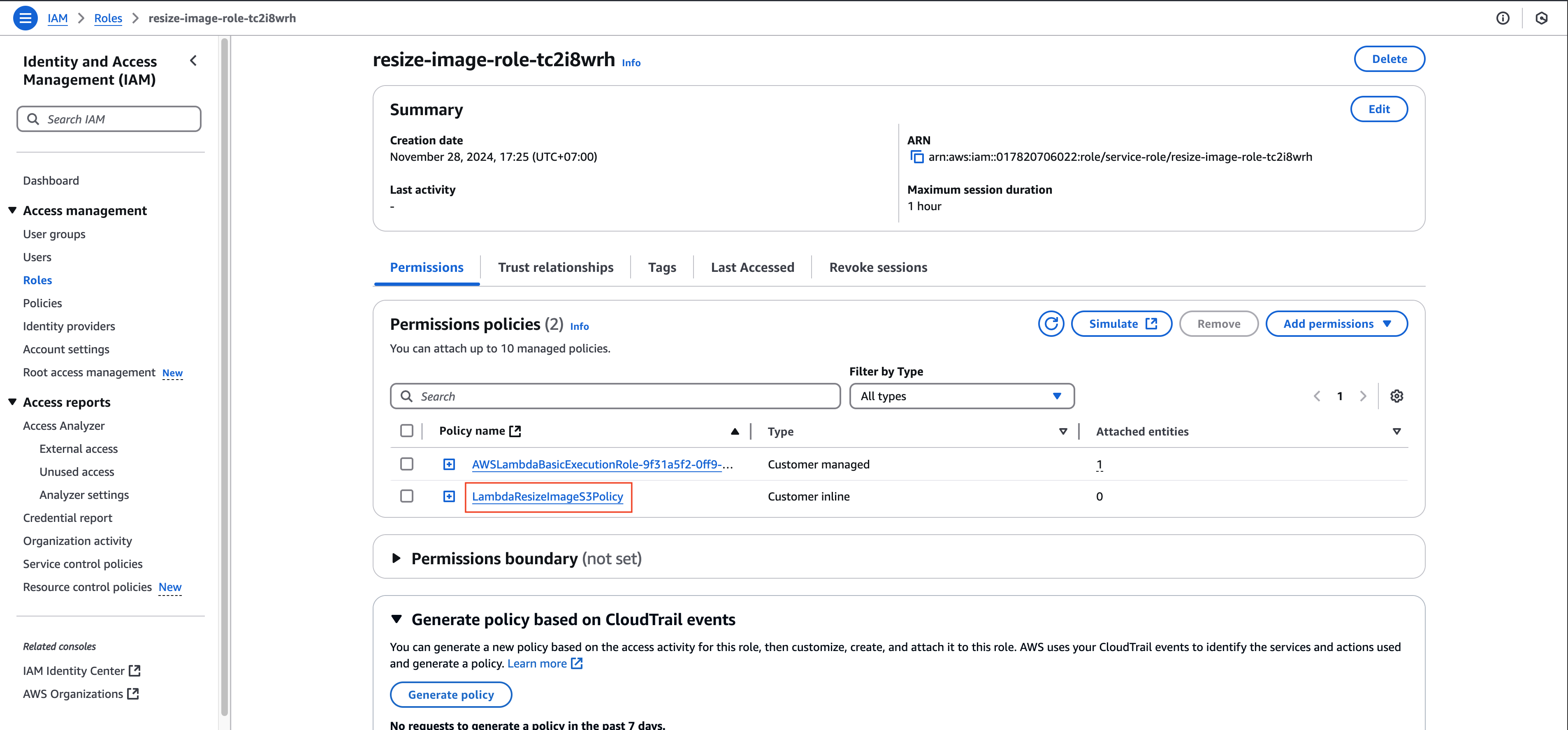
You have now successfully configured the IAM policy granting your Lambda function the required permissions to interact with both S3 buckets. The next step is to test the Lambda function by uploading an image to verify the complete workflow.